The Internet of Things relies heavily on cloud technology. The large amounts of data collected from sensors and smart machines surpass the storage capacity of many on-site factory computers. The cloud is needed to not only store these large amounts of data, but also process it.
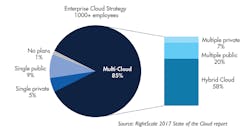
In January 2017, Right Scale, a leader in cloud-management services, conducted its sixth annual “State of the Cloud” survey. The survey asked 1,002 IT professionals about their adoption of cloud infrastructure and related technologies. Out of the 1,002 respondents, 48% of the respondents represented companies with more than 1,000 employees. Of the enterprises surveyed, 85% stated that they have a multi-cloud strategy with several public and private cloud services. This is up 82% from 2016. Among those companies, 32% run computing workloads in public cloud and 43% in private cloud services.
The graph shows the cloud service pattern for major IT enterprises. (Courtesy of Right Scale)
The piece of the puzzle that connects cloud computing to factory line devices is called “the fog.” What is the fog or fog computing? According to the OpenFog Consortium, the “fog bridges the cloud-to-things continuum.” It is a system-level horizontal architecture that handles the distribution of computing, storage, and networking, bringing it closer to the user and their devices. Fog computing has three essential attributes:
- Horizontal architecture: Supports multiple industries applications domains, while delivering intelligence and services to users and business.
- Cloud-to-things continuum: Fog enables services to be distributed closer to things, and anywhere along the continuum between cloud and things.
- System level: Fog computes at a system level. It extends from the things, over the network edges, through the cloud, and across multiple protocol layers.
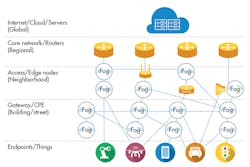
Shown is the cloud-to-fog-to-edge connection map, which illustrates how the cloud connects to edge nodes and how nodes connect to end devices.
The fog works by first connecting the cloud servers to routers. The routers and their data connect to edge nodes. These edge nodes connect to gateways that ultimately connect to endpoints, such as robotic arms or smart devices. By using edge nodes, the data and computing power is brought closer to the devices and helps those devices not rely on cloud servers.
The International Data Corporation predicts that by 2025, 45% of the world’s data will be moved closer to network edge services and devices. Fog computing offers security to ensure safe, trusted transactions; awareness of client-centric objectives; real-time processing and cyber-physical system control; and pooling of resources from free end-user devices.
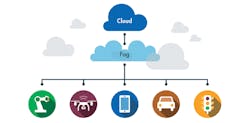
The fog brings computing power closer to the everyday devices engineers interact with, such as robotic arms and smartphones.
My recent interview with Andrew Kling, Director of Cyber Security and Architecture at Schneider Electric, defined how the cloud and fog work together. According to Kling, “Everyone has their own definition of cloud, but generally it's known as a compute resource and it is a remote resource that you connect to. Fog computing is about bringing a job that is closer to the edge. So, think of the cloud coming down to the ground aka as fog. Schneider Electric is part of that consortium and we're helping drive those concepts.”
By bringing the computing power down to the edge, devices can work together. Kling explains “the ability to actually process that data and information closer to the edge is really what we're trying to accomplish. Companies and engineers involved in fog technologies are trying to accomplish that you can share that information east and west rather than north and south; sharing the edge information from one edge device to another one. A machine can talk to another machine and they can cooperate at that point without having to go to a server process.”