The Internet of Things (IoT) describes a network of intelligent devices connected to the internet for the purpose of remote control and monitoring. From infrastructure to commercial environments and logistics to manufacturing, this smart technology comprised of monitors, actuators, controllers, and other devices is being rapidly woven into an expanding range of applications and environments.
One area where the IoT opens new opportunities for innovation is the physical security of industrial operations and environments. There are cloud-based technologies available that can provide a better and more simplified means of controlling and monitoring access to devices, systems, and equipment. In equipment-level access applications, IoT-type systems can be used to provide real time monitoring of equipment status, in addition to feedback on maintenance and physical security, optimization, and efficiency of connected systems.
Leveraging Electronic Access to Improve Operations
Within any industrial operation, there are equipment and areas that need to be secured—for safety reasons as well as securing vital equipment from damage or loss. In many operations, this security is often very basic: A mechanical key is kept in a maintenance locker and tracked via paper records, for example.
Electronics access solutions (EAS) function within the larger IoT digital landscape, providing intelligent access and control to machines, production lines, and other types of sensitive and valuable items at the equipment level. Implementing electronic locking solutions in manufacturing and industrial settings involves adding electronic technology and software in place of physical locks and keys. Intelligent electronic locks are a key element of an electronic access solution, restricting access through the validation of user credentials via a connected user interface, like an RFID reader.
In certain situations, operations managers may have the perception that implementing EAS involves significant hardware and IT investment as well as ongoing support. However, implementing this type of technology is relatively easy and very cost-effective, especially when industrial operations are expanding internet-based networks in their facilities. In addition, these systems provide crucial data that can be leveraged to enhance productivity in unique ways.
Enhancing Logistics and Safety
One of the core advantages offered by implementing IoT architectures is the virtual flood of new information that intelligent sensors, controllers, and other networked devices will provide. New data collected from the IoT will require new analytics systems to allow companies to best leverage this additional information. Organizations will need to shift from traditional methods used for gathering data, such as spreadsheets and manual data entry, to software or cloud-based analysis and monitoring.
Electronic access offers many solutions for remote access control and monitoring within the industrial environment.
Logistics
Cloud-based electronic access, for instance, can provide useful logistics and operational information to industrial managers. Many industrial operations have supply cabinets, equipment lockers, and Maintenance, Repair and Operations (MRO) cabinets that are routinely secured. When equipped with EAS technology, access and withdrawal of items from these secured locations can be precisely tracked—not only to the cabinet itself, but down to the individual supply bins within the cabinet.
Only authorized users can access these cabinets; they are logged in. The items they remove are tracked, with the data sent back up into the cloud so that the suppliers can then monitor supplies and replenish them instantaneously. This provides additional benefit to the operations team, as they can analyze usage data to run more efficiently and optimize their inventory levels.
Safety
EAS technology can also enhance safety, a vital and ongoing concern in many industrial environments. There may be portable equipment secured in lockers, or complex and sensitive machinery (such as costly machine tools) that are only to be accessed and operated by trained, certified personnel.
EAS can ensure that only authorized personnel are allowed to operate potentially dangerous equipment or access dangerous product, by providing electronic keys to access these resources; if a machine tool enclosure is opened and maintenance and repair is conducted, this approach tracks exactly which technician performed the work. These connected devices can also provide data on how much time a machine tool’s enclosure was open, helping operations managers to assess machine downtime and costs.
Efficiency
More efficient use of manufacturing supplies is another advantage offered by the data generated with electronic access systems. For example, the auto collision industry experiences up to 30% waste due to inefficient use of materials. A cloud-based inventory management system can easily eliminate this waste, increasing bottom line profits by as much as 30%.
Using a web-based access system, technicians log in when they need materials, and the products they pull are tracked according to the repair they are working on. As a result, cost control and materials management can be improved, and work materials inventory can be more precisely controlled based on actual consumption.
Digital “Keys” Improve Access Control
In many applications, accessing machines or supply cabinets requires entering a password into a keypad or machine user interface. While this is a step up from physical keys, it doesn’t take full advantage of the efficiency and flexibility that cloud-based EAS platforms supply.
As manufacturing environments become more connected and IoT-equipped, it is possible to implement a more flexible and efficient way of providing the right users with digital “keys” that both enhance security and make physical access easier for personnel. They use smartphones or RFID cards to provide electronic access credentials that are extremely secure and much easier to manage and update.
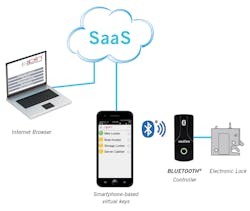
Smartphone access: A Bluetooth enabled smartphone is an effective “key” to access equipment with electronic locking mechanisms. Individuals who are to be authorized for accessing equipment—technicians performing maintenance or personnel removing materials from an MRO locker—will have a smartphone app on their phones. Time-based virtual keys can be sent wirelessly to the app via a cloud-based web portal.
To access the secured equipment, the technician touches the access button on their installed app, which transmits the encrypted Bluetooth signal to the lock controller, unlocking the door and sending a record of the access via the smartphone app to the cloud.
Each lock controller has a unique, algorithm-based identity, which is stored in the remote web portal database. The Bluetooth device does not require a wireless network to open the lock; the smartphone simply communicates via Bluetooth with the lock controller. Each time access occurs, a digital audit trail is generated and sent using a wireless network connection to the remote web portal, via the cloud.
This is a highly secure approach. The electronic key loaded to the app will typically have a limited timeframe during which it can be used. If it expires, the technician must access the cloud again in order to be reauthorized. In addition, the Bluetooth signal has 128-bit encryption, protecting it from the risk of hacking.
Bluetooth technology is gaining wider acceptance in industrial IoT settings, with the recently adopted Bluetooth mesh networking supporting many-to-many communication over Bluetooth radio designed specifically for industrial environments.
RFID access: An alternative to Bluetooth access via smartphone is providing remote access through the use of RFID technology. Users can access the equipment with traditional RFID cards, following the same basic protocol. The Bluetooth-enabled lock controller periodically uploads and downloads credential information via a Bluetooth-enabled device connected to the cloud, such as a wireless tablet.
The audit trail is pushed from the Bluetooth controller to a wireless device and up to the cloud, where it can then be accessed by the equipment owner’s operations office. Administrators can remotely assign and revoke RFID cards using the same cloud-based web portal.
This is a convenient approach for settings where smartphones are not permitted to be used, including factory floors where there is proprietary equipment or a work rule restricting smartphone usage.
EAS: Physical Security and IoT Data
Cloud-based EAS platforms provide unique and valuable information for machine designers and manufacturers implementing IoT-level connectivity and intelligence in their enterprise systems. These solutions provide a level of physical security that is extremely flexible and much more secure than mechanical keys, all the while delivering real-time access tracking and control of valuable equipment and resources for facility protection and safety.
Similar to other IoT-type systems, EAS technology can be used to generate valuable information about facilities uptime and utilization, personnel efficiency and manufacturing costs. As with other types of information generated by IoT technology, it is ultimately up to the enterprise to intelligently mine and analyze this data and apply it to their business challenges.
Steve Spatig is general manager, Electronic Access Solutions, at Southco, Inc.