In spite of recent slowdowns in the initial expansion of the Internet of Things (IoT), strong long-term growth is still projected throughout the next decade. Some are even predicting a doubling of the industrial sector IoT in the next couple of years. Most of us imagine that growth will consist largely of new IIoT-ready equipment, smart sensors and controls, and that old plants filled with legacy machinery will be ripped up and replaced to fulfill industrial Internet of Things (IIoT) dreams.
While it can’t be denied that new technologies for computing and connectivity enable daring new IoT applications, there is still a huge potential to apply the same technologies to existing legacy sites and equipment. Doing so can address longstanding problems in industrial automation, as well as support new functions such as predictive maintenance and big data analytics. Let’s explore a few of these issues and opportunities for legacy upgrades and how IoT technologies can be brought to bear.
Secure Infrastructure
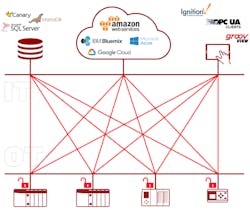
In industry surveys of executives and developers, cybersecurity always ranks as a top IoT concern. However, security is an issue for industrial automation, generally. The frequency and destructiveness of cyberattacks are increasing, especially for industrial targets, and as information technology (IT) and operations technology (OT) converge, there are more opportunities for security breaches. The typical architecture involves many point-to-point connections, using unsecured application- and device-specific communication protocols (see image below). As these networks grow, the number of potential weak spots grows. It’s impossible to imagine high-volume, autonomous data exchange in such a vulnerable environment. The slow progress of new IoT projects has been attributed to security risk alone, but existing plants and equipment are no less at risk.
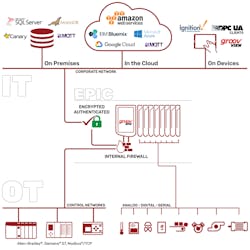
This has pushed vendors to embed stronger security into industrial edge devices. The latest generation is designed to operate in dangerous cyber environments and to create resilient infrastructure. These devices make it easier to implement best practices with ingrained security features such as user authentication, internal firewalls for blocking unsolicited requests and multiple network interfaces for segregating trusted and untrusted traffic. They can also take advantage of secure, network-oriented communication protocols and SSL/TLS encryption and certification for exchanging data on the internet.
In the context of IIoT, these features are essential, but engineers are also taking advantage of them to better protect already installed equipment and plants. A single, low-cost edge device can sit between existing machines and unsecured network segments, immediately reducing the number of targets exposed to cyberattacks. The same device can also connect network segments separated physically or by subnets, VLANs or firewalls. This connection lays the groundwork for an IIoT-ready infrastructure.
Unlocking Operational Data
With a secure foundation in place, other IIoT technologies that access the untapped potential of legacy equipment can be introduced. One of these is the MQTT communications protocol (formerly MQ Telemetry Transport). MQTT is one of the most popular IoT-specific protocols. It’s used by or with popular consumer and enterprise applications including Facebook Messenger, Raspberry Pi, Amazon Web Services and other major cloud computing platforms. It makes smart energy, health and banking services possible, and is growing in popularity for industrial IoT as well.
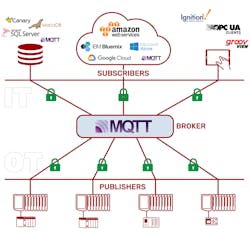
MQTT differs from typical communication protocols for industrial connectivity by doing away with the point-to-point, poll-response model in favor of a publish-subscribe model, which consumes much less bandwidth. In a poll-response model, devices send all their data every update cycle, even if nothing has changed. In a publish-subscribe model, on the other hand, each device on the network transmits (publishes) data only if it changes. All that data is sent to a central server (called a broker) which, like Twitter for machines, broadcasts updates but only to network clients that have chosen to follow (subscribe to) these updates.
Not only does this reduce bandwidth consumption (by 80 to 95% according to industry leader Cirrus Link Solutions), it also dramatically simplifies network architectures. Each network client requires only a single outbound connection to a common MQTT server to consume and share data with any other software or device client. As a result, MQTT networks can scale to millions of connections—maintenance databases, performance monitoring tools, inventory and invoicing systems, and cloud-based analytics platforms—creating the kind of infrastructure needed to support serious IIoT applications. And again, when built on a secure OT layer, it’s just as feasible to integrate data from legacy equipment as from new.
Remote Management
In addition to increasing security and connectivity, IIoT is driving the trend of increased processing power and storage in edge devices. For control systems, this brings general-purpose computing power to the equipment level and makes it possible to run many kinds of software in the field.
For OEMs and system integrators, it can take years of sales, design, and development to get a product or system to the start-up phase, but that’s also just the beginning of its serviceable life. There may be decades of troubleshooting, software updates, and system expansions to follow. Instead of sending technicians into the field or exchanging spreadsheets and photographs with end-users, many companies might like to take advantage of virtual private networks (VPNs) to facilitate these activities.
VPNs connect private networks across the public internet so that clients on both sides can communicate as securely as if they were on the same network. Engineers can interact directly with remote equipment, making it easier to diagnose problems or deploy fixes before problems occur.
Although VPNs are common in business systems, they have been a difficult proposition for automation. Gaining VPN access to remote equipment has historically required that end-user’s IT staff grant external access to their VPN servers, assuming there were already connections between IT and OT networks. Not only might this create security fears among end-users, the additional infrastructure and maintenance required to support a single external vendor might be deemed infeasible.
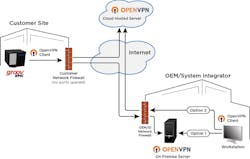
Now, however, industrial edge devices have the power to run their own VPN clients. Once configured, they can establish device-originating connections to remote VPN servers. Because the connections are outbound, it isn’t necessary to modify the end-user’s firewall or authorize external access for the OEM or SI, which reduces security concerns and lifts the burden of IT overhead from the end-user. A single supplier can support a distributed installed base using their own on-premises or cloud-hosted VPN servers, making a much more feasible and affordable business case for providing remote lifecycle support.
Edge computing has disrupted the consumer sector by bringing complementary functions together in mobile devices, right where they are needed. The same thing is happening in the industrial sector. Combining smart industrial-edge devices with enterprise security and communication features makes it possible to quickly set up a framework for addressing problems and realizing new possibilities. Engineers can use the framework to create a secure, scalable, serviceable infrastructure that lets them bring their legacy equipment and systems into the IIoT age. The same framework of technologies also makes possible other kinds of forward-looking functions for legacy sites, including: • Text and email notifications. • Mobile control panels and operations dashboards. • Embedded databases for machine control. • Distributed processing and connections. • Custom applications at the process level.
There’s no need to reserve this kind of innovation for your next redesign, nor is it necessary to rip out your legacy equipment to put these technologies to work. Rather, by adopting the approach described here, you can pave the way past the obstacles preventing IIoT proliferation.
Josh Eastburn is director of technical marketing for Opto 22.