Protecting OT Networks with Industrial Intrusion Prevention
Cybersecurity incidents are crippling critical industrial infrastructure and harming businesses. Some are targeted attacks, such as ransomware attacks, while others are nontargeted incidents, such as contamination through malware that gains access to unauthorized computers and spreads across entire industrial control networks.
Creating a zone-based industrial network architecture can reduce the damage these incidents cause. In the meantime, cybersecurity experts propose more proactive measures to protect industrial networks. These can be established by an industrial intrusion prevention system (IPS), which counteracts intrusions and reduces their impact on industrial systems.
An IPS is a form of network security designed to detect and block identified threats by constantly monitoring networks, looking for possible malicious cyber incidents and logging information about them. It features deep packet inspection (DPI) technology, which enhances network security visibility and ultimately helps mitigate risks and protect industrial networks from security threats.
Although IPSs have worked well on IT networks for a while, they are difficult to deploy in OT networks because the first priority of OT networks is availability and performance, and the first priority of IT cybersecurity is confidentiality. Implementing an IPS in OT networks without considering the daily operational requirements of OT engineers could block control commands needed for critical production and disrupt operations.
To fulfill OT cybersecurity requirements, it is essential to use OT-centric DPI technology. OT-centric DPI can identify a host of industrial protocols and allow or block specific functions, such as read or write access. Based on the identified protocol, an IPS can prevent any unauthorized protocols or functions. This ensures traffic on industrial networks is trusted and not malicious.
Whitelisting control is an approve-and-go mechanism that only grants access to authorized devices, service, protocol format, and control commands on a whitelist. It ensures all network activity on industrial networks is authorized and network operators can define access controls at different levels depending on operational requirements. For example, OT engineers can compile a whitelist of devices and services or IP ports that can access all or part of the network. In addition, it can also define the authorized protocol format to prevent unauthorized commands from passing through networks.
What’s more, OT engineers can even define which control commands can pass through the network to reduce human error associated with sending a wrong control command. With whitelisting control, the likelihood of a denial-of-service attack by OT Trojans can be significantly reduced.
An IPS can handle several scenarios, including:
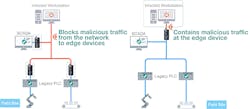
Blocking and containing malicious traffic. IPSs protect industrial networks by blocking malicious traffic going from the network to edge devices and containing malicious traffic at edge devices. They can be placed in front of critical assets such as PLCs and HMIs to improve network security and ensure network availability while protecting critical assets from being manipulated by malicious actors.
For example, when a workstation is being infected with malware, the malware can often spread to as many devices and networks as possible. It could spread to most of the network’s devices before an OT engineer or network operator even notices it.
Therefore, both proactive actions are important to mitigate the risks. One action blocks malicious traffic at the first place when the network is contaminated; the other contains it to a manageable degree if it unfortunately happens.
Virtual patching. Patching significantly reduces a system’s exposure to cyberthreats. However, it continues to be a critical challenge in OT environments. Devices on industrial controls are not always available for updates when vulnerabilities are identified. For example, a production operation remains up-and-running until its next scheduled maintenance.
Sometimes, updates are not feasible because devices on industrial controls may have already passed their predicted life and vendors are no longer providing updates. Virtual patching can help complement existing patch management processes by shielding against vulnerabilities. Virtual patching acts as an agentless emergency security tool OT administrators and operators can use to quickly remedy vulnerabilities on affected OT equipment.
To pursue operational efficiency and availability, it is always important to consider cybersecurity. The idea that OT networks are isolated and secure has been cut down to size by several recent cybersecurity incidents in manufacturing plants. Two different approaches can be taken to enhance network security. One is to ensure your industrial networks have a secure foundation or network infrastructure that lets authorized traffic flow to the correct places. Alternatively, you can identify critical assets and give them layered, proactive protection such as an IPS and whitelisting control.
An IPS continuously monitors network traffic entering and leaving an industrial organization’s network, watching for suspicious or malicious traffic, alerting IT and taking action to stop the traffic. Although this approach can easily be used IT networks, implementing IPS in OT must consider the requirements of OT engineers to avoid disrupting operations.
Felipe Sabino Costa is an electrical and electronics engineer and an ISA/IEC-62443 industrial cybersecurity instructor for the International Society of Automation. He is also a Latin American industrial cybersecurity expert at Moxa.
About the Author
Felipe Sabino Costa
Latin American Industrial Cybersecurity Expert, Moxa
Felipe Sabino Costa is an electrical and electronics engineer and an ISA/IEC-62443 industrial cybersecurity instructor for the International Society of Automation. He is also a Latin American industrial cybersecurity expert at Moxa.